Practice Areas
Cybersecurity, Data Protection & Privacy
- Get free trial for practice areas as below
- Business
- Consumer
- Corporations
- Criminal
- Employment
- Family
- General Counsel
- Governance
- Immigration
- Intellectual Property
- Personal Injury NSW
- Personal Injury Qld
- Personal Injury Vic
- Personal Property Security
- Property
- Succession
- Work Health & Safety
- Tax
- Mergers & Acquisitions
- Banking & Finance
- Social Justice
- Cybersecurity, Data Protection & Privacy
- Insolvency
- Competition
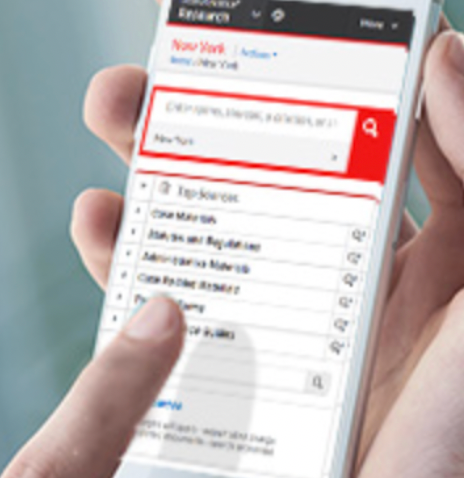
LexisNexis Practical Guidance®
Straightforward guidance across a range of topics
Cybersecurity strategy — Checklist for Overall cybersecurity strategy
| Introductory note: |
| This checklist aids an organisation in managing cybersecurity risk by addressing key general data security considerations for business entities. |
| This guideline is based on ASIC's Report 429 (Cyber resilience: Health Check), ASIC’s Report 468 (Cyber resilience assessment report), ASIC’s Cyber Health Check Report and the US National Institute of Standards and Technology (NIST) Cybersecurity Framework. It is aimed at better managing cybersecurity risks but is not a one-size-fits-all approach. |
| How to use this checklist: |
| This checklist is not a one-size-fits-all approach. Different organisations will have unique risks, threats and vulnerabilities, and will implement their staff training strategy with differing priorities. Instead this checklist is designed to |
| Other notes: |
| The guideline is a living document and will continue to be updated as new technologies, threats, risks, and solutions arise. |
| Links to related content: |
| For further practical guidance on data security audits, see Personal Data Security Breach Management. |