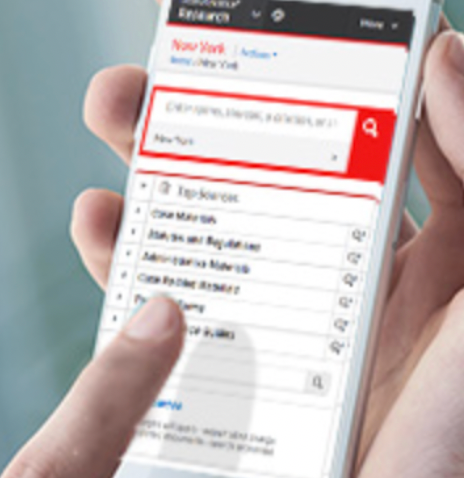
- Get free trial for practice areas as below
- Business
- Consumer
- Corporations
- Criminal
- Employment
- Family
- General Counsel
- Governance
- Immigration
- Intellectual Property
- Personal Injury NSW
- Personal Injury Qld
- Personal Injury Vic
- Personal Property Security
- Property
- Succession
- Work Health & Safety
- Tax
- Mergers & Acquisitions
- Banking & Finance
- Social Justice
- Cybersecurity, Data Protection & Privacy
- Insolvency
- Competition
- Cybersecurity strategy
- Ensuring data protection compliance
Induction and training
Policies and procedures buried on the intranet or forgotten at the bottom of the drawer will not impact the cybersecurity risks faced by your organisation. In order to be effective policies and procedures must be integrated in data to day operations, be used in decision making and training, and be revised and updated in response to changes in technology, changes to the business and experience with risks and incidents. If not implemented, your well-documented strategy can serve as a benchmark available to be called upon as evidence of proper practice should a third party claim or formal investigation by a regulator take place as a result of a security incident. It is vital that your security strategy be embedded in the operational life cycle of your organisation.
See Induction and training.